Erase iPhone Remotely, In this guide, we’ll walk you through the process of remotely erasing your iPhone for enhanced security and privacy.
Preparing for Remote Erasure
Backup Your iPhone Data: Before erasing your iPhone, ensure you’ve backed up your data using iCloud or iTunes. This safeguards your important information.
Disconnect Apple ID and iCloud Account: To prevent any issues during erasure, disconnect your Apple ID and iCloud account from the device.
Remote Erasure Methods
Using ‘Find My’ App
Enable ‘Find My’ on Your iPhone: Go to Settings > [Your Name] > Find My > Find My iPhone. Turn on “Find My iPhone” and “Send Last Location.”
Access ‘Find My’ from Another Device: Visit iCloud.com or use another Apple device. Sign in to your Apple ID and access the “Find My” feature.
Remote Erasure through iCloud
Access iCloud’s Website: Visit iCloud.com and log in to your Apple ID.
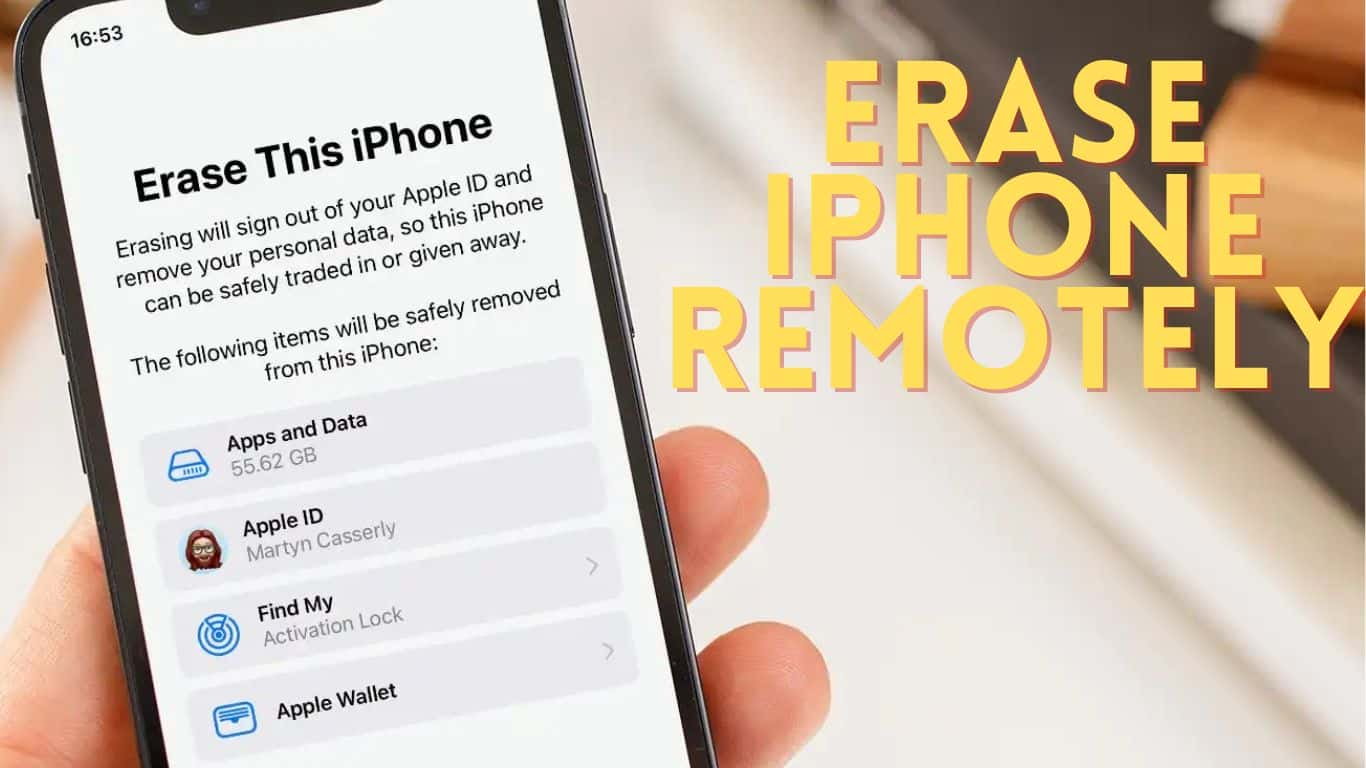
Initiating Remote Erasure: Choose “All Devices,” select your iPhone, and click “Erase iPhone.” Confirm the action.
Remote Erasure via iTunes
Connect Your iPhone to a Trusted Computer: Use a USB cable to connect your iPhone to a computer with iTunes installed.
Initiating Remote Erasure: Open iTunes and select your device. Click “Restore iPhone” and confirm to initiate remote erasure.
Understanding Remote Erasure Modes
Erase All Content and Settings
Complete Data Wipe: This mode performs a factory reset, wiping all data on your device.
When to Use This Option: When selling or giving away your device, or if it’s lost/stolen.
Erasing Data Remotely but Preserving Settings
Deleting Personal Data: This mode erases personal content while retaining system settings.
Situations for This Mode: When troubleshooting issues without affecting system settings.
Confirming Erasure and Checking Completion
Receiving Erasure Confirmation: After initiating erasure, you’ll receive a confirmation on the device.
Checking Erasure Status: If the device is offline during erasure, it will start once connected.
Handling Activation Lock
What is Activation Lock?: Activation Lock prevents unauthorized access to your device.
Disabling Activation Lock: After erasure, your Apple ID credentials are required to reactivate the device.
Additional Security Measures
Two-Factor Authentication
Enhance Apple ID Security: Enable Two-Factor Authentication for an added layer of protection.
Impact on Remote Erasure: Two-factor authentication enhances security during remote erasure.
Data Encryption and Remote Erasure
Understanding iPhone’s Data Encryption: iPhones are encrypted by default, enhancing data security.
Encryption’s Impact on Remote Erasure: Encryption ensures erased data is almost impossible to recover.
Remote Erasure and Third-Party Apps
Compatibility and Considerations: Not all third-party apps offer remote erasure. Choose reputable options.
Recommended Apps for Added Security: Look for apps that align with Apple’s security standards.
Frequently Asked Questions
Can I Undo a Remote Erasure?
Remote erasure is irreversible; there’s no way to recover erased data.
Does Remote Erasure Delete System Updates?
Remote erasure doesn’t affect system updates.
How Long Does Remote Erasure Take?
Erasure duration depends on data size, typically taking a few minutes.
What Happens If My iPhone is Offline?
Erasure begins when the device is online.
Can Remote Erasure Be Tracked?
Erasure doesn’t track your device; it’s designed for privacy.
Conclusion
Remote erasure is a vital tool for safeguarding your iPhone’s data. By following these steps and understanding the modes and security measures, you can confidently protect your personal information.

Im more than happy to uncover this website. I wanted to thank you for your time due to this fantastic read!! I definitely enjoyed every part of it and i also have you bookmarked to see new things in your site.