Table of Contents
We have just seen APKTOOL and JDGUI Tool in the previous post. Now we are going to see another very useful tool bytecode viewer, this tool actually makes use of both Apktool and JDGUI in the background. In this post, we will see how to make use of Bytecode viewer
How to use Bytecode Viewer Tool
Download the latest version of Bytecode viewer from the GitHub

You can run this tool on several platforms, with bytecode viewer you upload an APK, and after some processing it presents the APKs decompiled Java source as well as the bytecode and Smali all in a single user interface, so you can have a comparison of the Smali versus the Java or rather the decompiled Java.
Instead of running APKtool, enjarify, JDGUI etc, you can just use this single tool which pretty much automates the process while offering a nice UI along with some additional utilities
Download the sample apk which we will decompile with Bytecode viewer. You can download any file and and rename it as you want
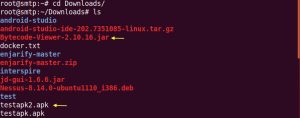
So let’s go to the folder where we downloaded it. I have download Bytecode viewer into the Downloads directory
# sudo cd Downloads
# sudo ls
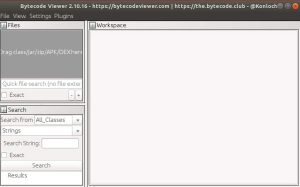
Run the following command and this will launch Bytecode viewer
# sudo java -jar Bytecodeviewer-2.10.16.jar
Once the Bytecode viewer opens, you can select the sample apk file to decompile. Simply, click on add from the menu and select your apk file to decompile
Here, I am going to select my apk file, named testapk2
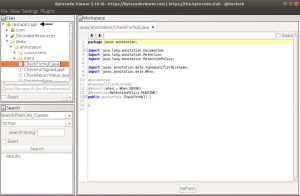
We just uploaded an APK without having the source code of the application and using some java decompilers. In this case fernflower, we have almost Java source. Now there are different Java decompilers bundled with Bytecode viewer so you can choose which one to use.
We will have a look at this later on during the analysis part of this Android series, but this tool is a great tool for static analysis.
Also Read : Decompile APK files with APKTOOL
Video Tutorial
That’s all, in this tutorial we have learned how to decompile APK files using Bytecode viewer. We will have a look at this tool in more detail during the reverse engineering part of this Android series. Comment on this post if you have any queries, I will be happy to help you.
