In this post, we are going to learn a Network Security specifically, configuring ssh-based Remote Access. We will use ssh to log in to the Linux server and authenticate so that we will be secure in critical connection.
Every time, whenever we change the server then we have to log in with a username and password. Fortunately, if you have a large number of servers constantly you are working with from any Linux console which you have ssh available, you can use a secure key and you can exchange keys with those systems so that once keys have an exchanged and confirmed they will authenticate you based on the known host value of your host as well as the security keys which you passed to that host.
Steps to Install OpenSSH
Before installing OpenSSH, verify the ssh first. Most Linux OS have preinstalled OpenSSH and some Linux don’t. So, let’s verify the SSH is installed or not.
Step 1
Verify the ssh with the -V command. If you have installed ssh then simply the output will be the version of ssh otherwise you will see a command not found. In my case, it is already installed. Go to Step 2 if your system not has been installed.
# sudo ssh -V
![]()
Step 2
Install the OpenSSH if your system doesn’t have preinstalled, following command will install the OpenSSH server so anyone can access the server via a secure shell, and from the OpenSSH client, you will be able to connect to another ssh server.
CentOS / RedHat
# sudo dnf install open-ssh server open-ssh clients
Ubuntu
# sudo apt-get install open-ssh server open-ssh clients
Step 3
Start and Enable the OpenSSH service.
CentOS / RedHat
# sudo systemctl start sshd.service
# sudo systemctl enable sshd.service
Ubuntu
# sudo /etc/init.d/ssh start
Connect Remote Host using Default Port
I have 2 hosts here with me that is RedHat 8 Enterprise and both machines have default SSH installed. I will show you, how do we connect through SSH from one machine to another machine.
RedHat 8 – 1 IP : 192.168.10.10
RedHat 8 – 2 IP : 192.168.10.20
So, we are going to ssh from RedHat 8-1 to RedHat 8-2 with the username “sshuser”. You can create any user for your Linux machine, my username is “sshuser” on “RedHat 8-2 with IP 192.168.10.20”
We are going to use the ssh -l command where ssh is a secure shell and -l is to specify the username which will be used to connect or login to the remote machine.
# sudo ssh -l sshuser 192.168.10.20
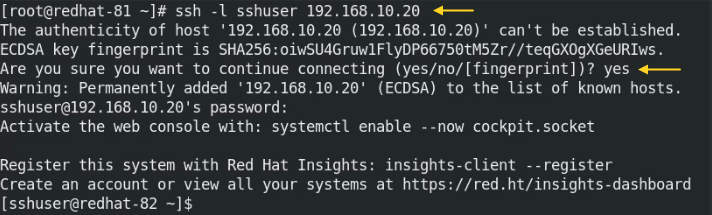
We can connect the host from another method by ssh command. In this command, we have removed -l and added @.
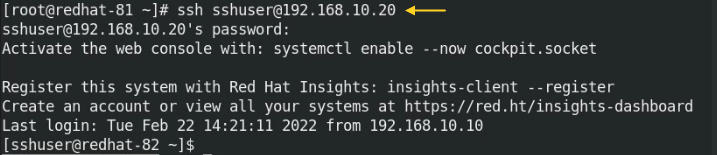
# sudo ssh sshuser@192.168.10.20
We can display the known hosts in the following directory. The known hosts automatically created during ssh to the remote host by accepting the connection with “Yes”.
# cat /root/.ssh/known_hosts
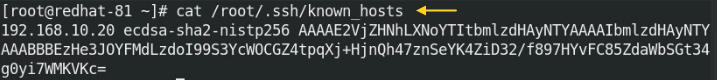
We can see the known hosts in the root directory because we have connected the host with the root user. If we connect the remote host with the user, we will find known hosts in the home directory.
How to login to a specific directory
Let’s say, we want to connect to the remote host with a specific directory. I am using remote host IP 192.168.10.20 and the specific directory is “/home/sshuser/“. We have two options, one is to connect remote host and navigate the directory with the “cd” command and the second option is using “-t“, directory path, and “bash“.
# sudo ssh -t sshuer@192.168.10.20 "cd /home/sshuser/ ; bash"
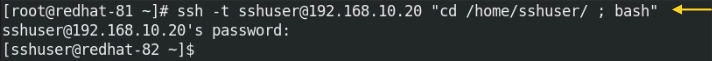
-t and the bash will help to execute the command which is between the two quotations and stay logged into the remote host. Verify the present working directory using “pwd” command.
# sudo pwd
![]()
Copy files on Remote Host using SCP
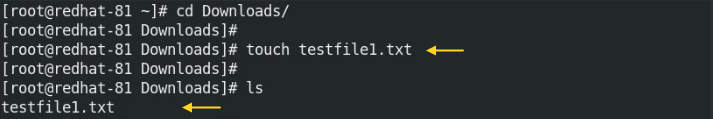
Create one test file to copy from one host to the remote host or you can copy any existing files. I am creating “testfile1.txt” file and this file will be copied from 192.168.10.10 to 192.168.10.20 into /home/sshuser/ directory.
We will create one text file and this file will be copied on the remote host.
# sudo touch testfile1.txt
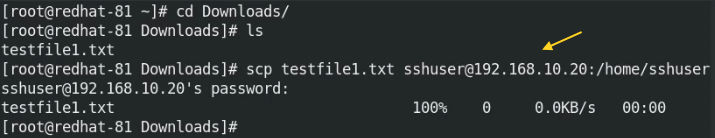
To copy files from one host to a remote host using scp.
# sudo scp testfile1.txt sshuser@192.168.10.20:/home/sshuser
Copy files from Remote Host using SCP
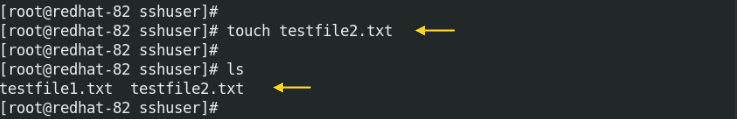
We can copy files from the remote hosts in a similar way of copy files to remote hosts. I have created “testfile2.txt” on the remote host. This file I will be copying from remote host “192.168.10.20” to “192.168.10.10”.
We will create one text file on the remote host “192.168.10.20.
# sudo touch testfile2.txt
Navigate any directory on the local host where you want to copy the file. I will be copying in the “Downloads” directory.
# sudo cd Downloads
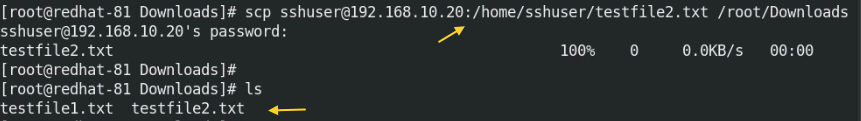
The “testfile2.txt” is located in /home/sshuser/ directory on a remote host which we are going to copy in the /root/Downloads directory on localhost.
# sudo scp sshuser@192.168.10.20:/home/sshuser/testfile2.txt /root/Downloads/
How to upload files using SFTP
SFTP is a secure file transfer protocol for accessing and managing the remote file system. SFTP is also helping to transfer files between hosts and it is more secure from FTP. Let’s see how can we connect SFTP on the remote host from the Linux terminal.
We have created one text file to upload from localhost to a remote host.
# sudo touch sftpfile.txt
# sudo sftp sshuser@192.168.10.20

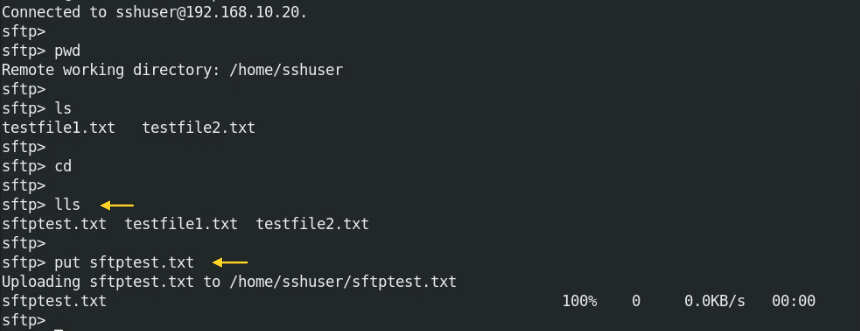
Check the present directory on the remote host. Write command without sftp> because you are already in sftp mode.
# sftp> pwd # sftp> ls # sftp> cd
Check the directory and files using “lls” command on the local machine.
# sftp> lls
Now, simply write a “put” command and file name which you need to upload on the remote host. I am going to upload “testfile1.txt” on the remote host.
# sftp> put testfile1.txt
To upload multiple files on the remote host, just type *. with the file extension.
# sftp> put *.txt
Connect Remote Host using different Port
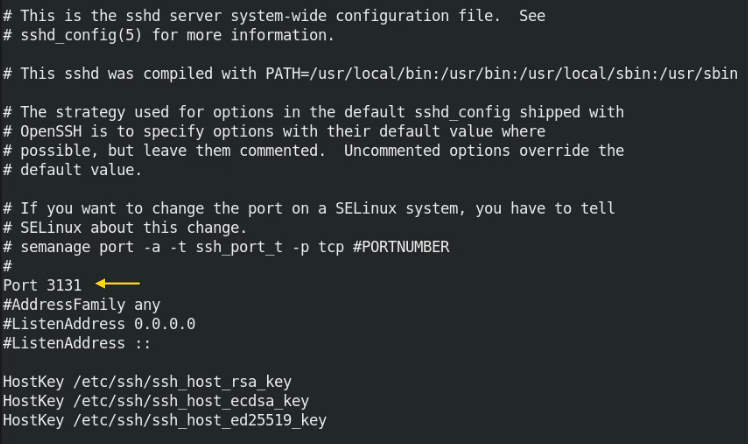
We will learn how to connect remote hosts using a different port. This step will make it more secure to the remote host if we change the default port from 22 to some other port. So, let me show you how we can change the default port, here I am using the port number “3131”, in your case you can use any port number. Login on the remote host and edit to /ssh/sshd_config file.
# sudo vi /etc/ssh/sshd_config
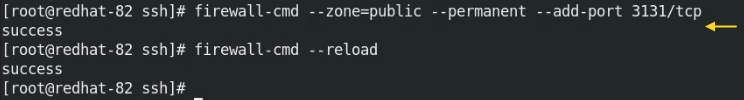
Once the port is changed in the sshd_config file, open and allow the port in the Firewall.
CentOS / RedHat
# sudo firewall-cmd --zone=public --permanent --add-port 3131/tcp
# sudo firewall-cmd --reload
Ubuntu
# sudo ufw allow 3131
# sudo ufw reload
Very important, open and Allow port in SELinux as well.
# sudo semanage port -a -t ssh_port_t -p tcp 3131
![]()
Restart the ssh services after changing and adding the port in Firewall and SELinux.
CentOS / RedHat
# sudo systemctl restart sshd.service
Ubuntu
# sudo /etc/init.d/ssh restart
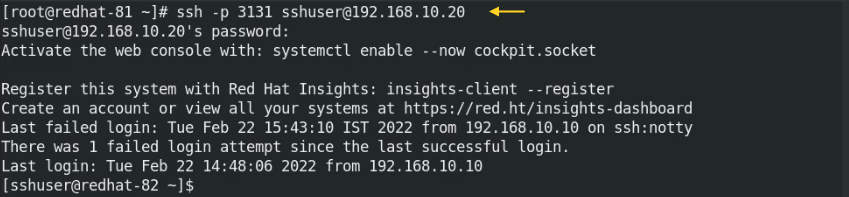
Finally, connect the remote host with changed port 3131.
# sudo ssh -p 3131 sshuer@192.168.10.20
So, we have seen how can we use OpenSSH in our day-by-day Linux Administration. OpenSSH is a very interesting thing in the Linux server and in this post, I have cleared how can we copy files through SCP and upload files throughout the SFTP. We have covered, how can we change the ssh default port from port 22 to 3131. You can put any port number but do not forget to add the changed port into a firewall and SELinux. By changing the port, we assume that it will be more secure because a hacker may try only a default port to attack your server.
Also Read : How to install and use SAR in RedHat 8 / CentOS 8
Also Read : Install Nagios monitoring tool on Ubuntu 20.04
Video Tutorial
That’s all, In this post, we have explained how to use OpenSSH. We have covered, SCP, SFTP, and how to change the default port. You can use PuTty to connect your remote server by changing port if you have changed the port as well as you can use WinSCP or any other FTP/SFTP Client to share the files from the Windows machine to the remote host.